Twilio, the company behind Authy suffered a data breach
Eleanore Beatty August 11, 2022 ArticleTwilio, the enterprise which owns the well known 2-factor authentication services Authy, has unveiled that it has experienced a details breach. An announcement printed on its web page states that some of its staff members fell victim to a phishing assault.
Twilio facts breach
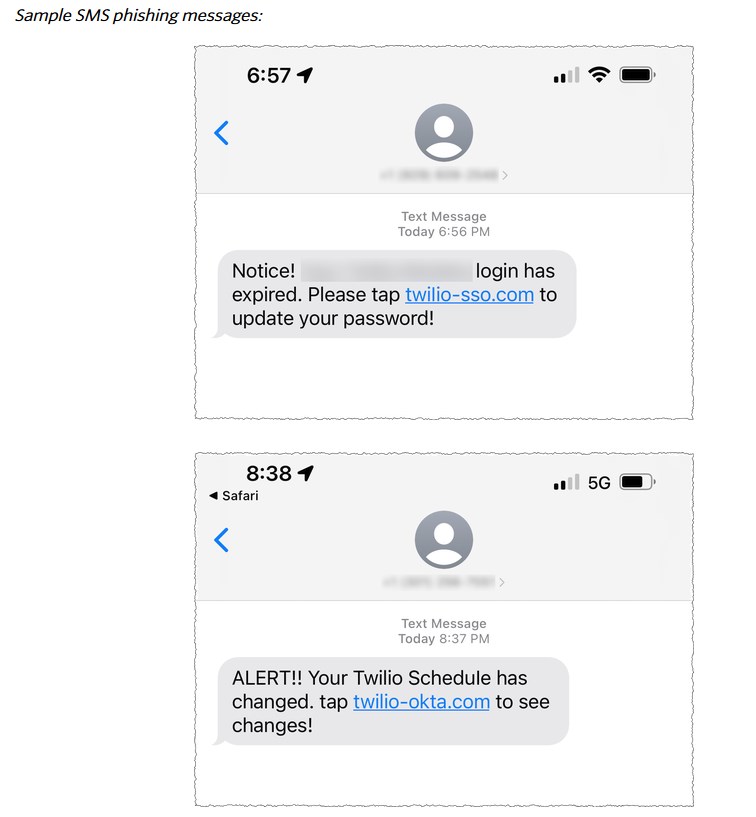
According to the report, hackers despatched some textual content messages to present-day and former workforce of the enterprise. The message which originated in the U.S., was spoofed as being sent from Twilio’s IT section, requested the end users to update their passwords. A website link, which accompanied the texts, directed the end users to URLs controlled by hackers, who then stole the credentials to attain entry to some of the company’s inner devices.
The concerning aspect is that the attackers were being capable to entry specified consumer details. Twilio is investigating the assault, and will notify prospects who ended up afflicted by the details breach. The enterprise has presently revoked accessibility to the compromised accounts. It says that it labored with US carriers to shut down the threats, and has taken down the accounts belonging to the attackers on internet hosting vendors that ended up made use of for the breach.
The transparency linked to the data breach might be appreciated by users, but the firm has not clarified what purchaser info was accessed. Twilio owns numerous merchandise and companies, Authy is just just one of people, and is likely the most well-known just one of the whole lot. The attack will no question increase some eyebrows about the protection of Authy.
Are Authy consumers safe?
There is no formal term irrespective of whether user details from Authy has been stolen. I have witnessed a handful of experiences on social media wherever customers are panicking. But, I believe it is protected to say that Authy users should not be nervous. Why is that?
1. Authy’s login process
2. Finish-to-stop encryption
Authy does not have a traditional login technique, i.e. a username and a password. Instead, the assistance makes use of your telephone number as your login ID. Let’s say a hacker in some way appreciates your telephone quantity, they can’t affiliate it with your account’s data. Since the TOTP assistance does not make use of a password technique, your credentials are not saved on the cloud, i.e. there is no password to be leaked. Authy makes use of a protection PIN (pass code) which serves as the encryption crucial to encrypt your knowledge (2FA account tokens) on your gadget in advance of it is uploaded to the cloud, this is acknowledged as end-to-finish encryption. The only person who has access to this encryption important, is the user, without the need of this crucial the info are unable to be accessed by anyone, even Authy itself can’t get the TOTP codes. In the same way, when you download Authy on a new system, you need to have to input the go code to decrypt the info, in advance of employing the application for 2FA codes.
This conclusion-to-end encryption is fundamentally identical to how cloud-dependent password administrators operate, for instance, Bitwarden. Even if a hacker has managed to breach Authy, your data must theoretically be protected for the reason that the contents are encrypted. That’s the complete issue of encryption.
This is not an official rationalization from the business, it is just dependent on my knowing of how finish-to-conclude encryption works. Of study course, it all depends on the correct implementation of the encryption procedure.
Some of my close friends rely on Authy across platforms (iOS, Android), but I moved absent from Authy a number of yrs ago, to Aegis due to the fact I prefer offline and open up supply applications. I utilized this tutorial for importing the tokens.
Do you use Authy?
Summary

Short article Title
Twilio, the organization behind Authy suffered a information breach
Description
Twilio, the corporation which owns the well-known 2FA company, Authy, has endured a information breach. This is what transpired.
Author
Ashwin
Publisher
Ghacks Know-how Information
Emblem

Ad
You may also like
Archives
- December 2024
- November 2024
- September 2024
- August 2024
- July 2024
- February 2024
- January 2024
- December 2023
- November 2023
- October 2023
- September 2023
- August 2023
- July 2023
- June 2023
- May 2023
- April 2023
- March 2023
- February 2023
- January 2023
- December 2022
- November 2022
- October 2022
- September 2022
- August 2022
- July 2022
- June 2022
- May 2022
- April 2022
- March 2022
- February 2022
- January 2022
- December 2021
- November 2021
- October 2021
Calendar
| M | T | W | T | F | S | S |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | |
| 7 | 8 | 9 | 10 | 11 | 12 | 13 |
| 14 | 15 | 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 | 26 | 27 |
| 28 | 29 | 30 | 31 | |||
